The Trust is responsible for all the personal data it has and takes its responsibilities extremely seriously. It takes every measure possible to protect the information it has.
Sometimes, the Trust needs to share the data it has with third parties. The Trust will only share data for a few, very specific reasons. For example, it is possible that we might need to share data for a new IT system which will help patient care; we might need to share data with the local authorities or other healthcare providers, or that we might need to examine how we are performing as a Trust by comparing patient data against others.
For more information on the legal basis behind the information sharing, please see the privacy notice here
When we are approached with a request to share our data we will examine very carefully every request where the data will be shared with others outside the Trust.
What we share, and how we share it will differ with every request. As part of the Trust’s commitment to “data protection be design” the Trust has published the guidance below to clarify what steps will be taken every time we are asked to consider sharing data, and what we expect of the requesting organisation.
- No data is to be shared without a decision from the relevant department
- No decision will be forthcoming without these processes being followed
- All data will be anonymised wherever possible
This process helps to balance the subject’s rights to privacy with the Trusts own requirements, both legal and operational.
We also hope staff members, and organisations who wish to use our data understand the steps required before the Trust will consider sharing the data.
There are several steps required for us to take before we can consider sharing data. To be transparent, this page sets out those steps we will undertake before we consider sharing data.
If we are asking another organisation to do something on our behalf, then we have a “controller-processor” relationship. There must be a written contract in place before we start.
The contract (or other legal act) sets out details of the processing including:
Contracts must set out:
- the subject matter and duration of the processing
- the nature and purpose of the processing
- the type of personal data and categories of data subject
- the controller’s obligations and rights
We also need to see the following points covered, usually included as terms or clauses:
- the processor must only act on the controller’s documented instructions, unless required by law to act without such instructions
- the processor must ensure that people processing the data are subject to a duty of confidence
- the processor must take appropriate measures to ensure the security of processing
- the processor must only engage a sub-processor with the controller’s prior authorisation and under a written contract
- the processor must take appropriate measures to help the controller respond to requests from individuals to exercise their rights
- taking into account the nature of processing and the information available, the processor must assist the controller in meeting its GDPR obligations in relation to the security of processing, the notification of personal data breaches and data protection impact assessments
- the processor must delete or return all personal data to the controller (at the controller’s choice) at the end of the contract, and the processor must also delete existing personal data unless the law requires its storage
- the processor must submit to audits and inspections. The processor must also give the controller whatever information it needs to ensure they are both meeting their Article 28 obligations
- If the supplier is providing an IT system the Trust must gather evidence they have appropriate certification
In addition to the contract, the Data Security & Protection team needs to evidence the following:
- Any supplier of IT systems which could impact on the delivery of care, or process personal identifiable data, has the appropriate certification that this is sufficient assurance for the Trust
- List of data security incidents – past or present – with current suppliers who handle personal information
- All Suppliers that process or have access to health or care personal confidential information have completed a Data Security and Protection Toolkit, or equivalent
What happens next?
The contract should be produced by a supplier and the DS&P team will need to confirm that the Trust is happy with the contract from a data security perspective: the DS&P team needs to decide whether the certification provides sufficient assurances, and judge the risks appropriately.
Once the contract is agreed the DS&P team will:
- Add the details to the Trust’s Asset Register, and the data flows will be mapped
- Ensure the risk register is updated to reflect any changes to the risk arising from the supply chain (where necessary)
- Ensure we offer support to the suppliers to resolve data security incidents
- Add the contract details to the list of suppliers, covering the products and services they deliver, their contact details and contract duration
If the relationship between the Trust and the third party is to share data then an Information Sharing Agreement (ISA) is required. There is a separate policy which details what is involved with the ISA. If we are approached by a third party looking to share data with us we would expect them to complete an ISA. There is a template here which can be used in its absence.
The Data Sharing Agreement will need to be approved by the Data Security & Protection (DS&P) Committee. No data sharing must take place without this agreement.
What happens next?
Once a completed ISA has been received, the DS&P team will perform the following checks on the third party:
- Their privacy policy is up to date and sufficient
- There has not been any action taken against them by the ICO
The ISA will need to be approved by the DS&P Committee. The dates are published on Connect and any ISA will need to be added to the agenda at least 1 week before the date of the Committee.
Once the ISA has been agreed the data can be shared. The DS&P team will amend the data flow maps where relevant. The staff member responsible for bringing the sharing agreement to Committee will be responsible for signing the sharing agreement and will need to agree who will become the Information Asset owner.
First, decide whether the project is clinical audit, research or service evaluation:
|
Clinical Audit |
Research |
Quality Improvement |
Service Evaluation |
|
Based on facts
Aims to evaluate how close current practice is to best practice
Aims to improve services
Never involves a new treatment
Do you want to measure current practice against evidence based clinical standards?
If the answer is Yes, it’s a Clinical Audit |
Aims to establish what best practice is
Is often a one off study
Aims to generate new knowledge / increase the sum of knowledge
Is theory driven
Do you want to investigate the effect of a new or existing treatment or technique on patients / carers? If the answer is Yes, it’s Research |
The use of methods and tools to continuously improve quality of care and outcomes for patients1 |
Designed and conducted solely to define or judge current care
Measures current service without reference to a standard
Usually involves analysis of existing data
Do you want to evaluate the effectiveness and / or efficiency of your current practice or service?
If the answer is Yes, it’s Service Evaluation |
Table 1.1
Clinical Audit:
In the first instance, contact the Clinical Audit Team on x31073 to discuss your project.
The clinical audit team will need a completed Clinical Audit Project Plan Template from you.
The project plan will be submitted for approval to the Trust R&D Governance Group which meets monthly (or directly to the Chair of the Committee when urgent).
We will also need your proposed audit tool (or questionnaire or data collection form).
Once approved, your project will now be registered on the Clinical Audit Programme.
What happens next?
The clinical audit can begin. The team require that the findings are:
- Findings must be documented in a report
- Action plan developed to improve below target compliance
- Any areas of risk identified should be escalated to your line or service manager for advice and immediate remedial actions
On completion, the clinical audit team require:
- A discussion in the findings and agree a process for sign-off
- Completion of the Clinical Audit Report Action Plan template
- Presentation of the report and action plan to a relevant Trust Committee to obtain sign off to implement your proposed action plan.
Research:
If your project is Research then the Trust always follows this process:
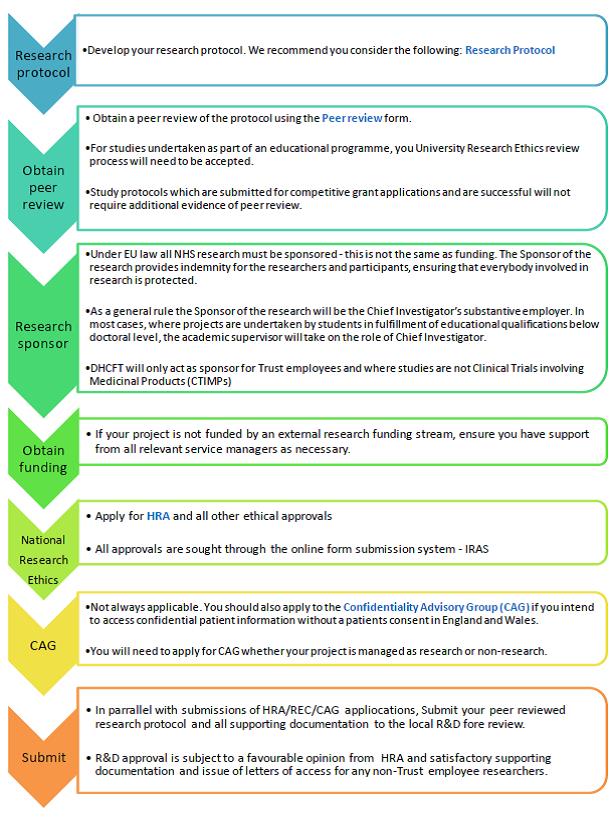
Table 1.2
|
STEP 1 |
Develop your Research Protocol |
*Develop your research protocol. We recommend you consider the following Research Protocol |
|
STEP 2 |
Obtain Peer Review |
*Obtain a peer review of the protocol using the Peer Review form. *For studies undertaken as part of an educational programme, you University Research Ethics review process will need to be accepted. *Study protocols which are submitted for competitive grant applications and are successful will not require additional evidence of peer review. |
|
STEP 3 |
Research Sponsor |
*Under EU law all NHS research must be sponsored - this is not the same as funding. The Sponsor of the research provides indemnity for the researchers and participants, ensuring that everybody involved in research is protected. *As a general rule the Sponsor of the research will be the Chief Investigator’s substantive employer. In most cases, where projects are undertaken by students in fulfilment of educational qualifications below doctoral level, the academic supervisor will take on the role of Chief Investigator. *DHCFT will only act as sponsor for Trust employees and where studies are not Clinical Trials involving Medicinal Products (CTIMPs)
|
|
STEP 4 |
Obtain Funding |
*If your project is not funded by an external research funding stream, ensure you have support from all relevant service managers as necessary. |
|
STEP 5 |
National Research Ethics |
*Apply for HRA and all other ethical approvals *All approvals are sought through the online form submission system - IRAS |
|
STEP 6 |
CAG |
*Not always applicable. You should also apply to the Confidentiality Advisory Group (CAG) if you intend to access confidential patient information without a patients consent in England and Wales. *You will need to apply for CAG whether your project is managed as research or non-research |
|
STEP 7 |
Submit |
*In parallel with submissions of HRA/REC/CAG applications, Submit your peer reviewed research protocol and all supporting documentation to the local R&D fore review. *R&D approval is subject to a favourable opinion from HRA and satisfactory supporting documentation and issue of letters of access for any non-Trust employee researchers |
Table 1.2 is summarised for audio purposes
Before the research project can begin the following will be considered and documented by the Trust in order to ensure the research project follows the appropriate safeguards:
- the research will not cause substantial damage or distress to the data subject (i.e. substantial physical harm, financial loss or psychological pain)
- medical research has approval from a research ethics committee (as defined in the new Data Protection Act) if it involves processing data in order to do or decide something with respect to an individual person
- the Trust has the appropriate safeguards in place that ensure respect for the principle of data minimisation and ensure that exemptions to data subjects’ rights are not exercised unless the rights are likely to render impossible or seriously impair the achievement of the purposes of the processing
- The processing is in the public interest (demonstrated over and above using ‘task in the public interest’ as the legal basis) if processing special category personal data
- The research must follow the Trusts policies and procedures
The Trust needs to know what data is being collected, where it is being used, and for what purpose.
What happens next?
If the research project has approval it can begin. The Trust requires:
We recognise the data subject has rights regarding what happened to their data. These rights can be waived IF following them would seriously impair the achievement of the research. This decision is made by the Trust
- Regular updates on the progress of the study
- Any amendments to the study to have HRA approval and R&D confirmation
- An end of study summary report to the R&D office as well as a report to the HRA.
Service Evaluation
Unlike clinical audit or research, a service evaluation is conducted solely to define or judge the current care or service provision. It answers the question ‘What standard does this service achieve?’
If you wish to evaluate a service then the Trust needs a protocol to be agreed by the local Research team.
What happens next?
The completed service evaluation will need to be reported back to the research team.
It is highly unlikely the Trust would share data outside of the above scenarios however if your requirements do not match any of the above scenarios then please contact the Data Security & Protection team on 01332 623700 x31121 or dhcft.datasecurityandprotection@nhs.net

